Understanding the pros and cons of modern biometrics in today's digital age
When you hear the word biometrics, what's the first thing that comes to mind? Biologists measuring a vial of cells? A science teacher's rubric for grading? Biometrics, at its core, is the perfect blend of “bio" (biology - the scientific study of life) and "metrics" (a system of measurement).
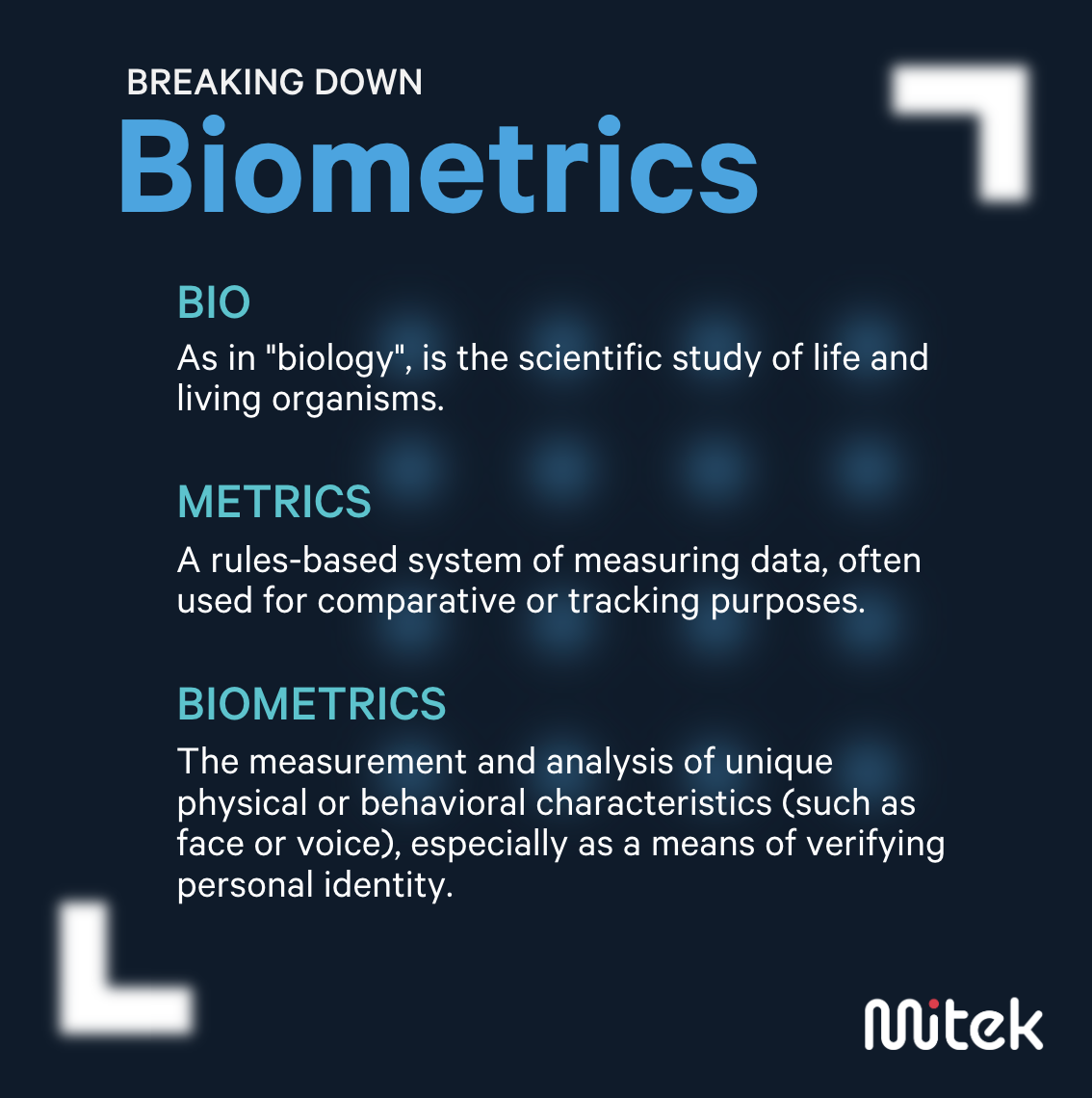
While biology is often qualitative, metrics are inherently quantitative. These two seemingly incongruous elements come together to create a cutting-edge technology that bridges the gap between physical reality and digital security. Today, biometrics are widely recognized as a more secure alternative to traditional authentication methods like passwords and PINs. In fact, 74% of consumers [1] now perceive physical biometrics to be the most secure method of digital identity verification.
In this article, we’ll delve into what biometrics are, how they work in authentication, and explore the advantages and disadvantages. We’ll also cover the latest trends and innovations shaping the future of biometrics.
Biometric types and their indicators: physiological and behavioral
If you've ever unlocked your mobile device with your finger, scanned your face to check your banking app, or yelled "Hey Alexa" to set a timer, congratulations! You've already used biometrics. These tools fall into one of two main categories: physiological and behavioral biometric indicators.
Facial recognition is starting to become the most used biometric in the world today to identify a person, replacing fingerprints. These biometrics can be classified as physiological biometric indicators. Comparing a person’s unique biological or behavioral traits, or rather something they “are”, against a pre-stored data set to verify their identity.
This analysis often occurs using devices like face-id or fingerprint scanners, both commonly in consumer devices such as smartphones, tablets, and laptops.
Keystroke dynamics, on the other hand, is considered a behavioral biometric, based on indicators such as typing speed. Behavioral biometric indicators are increasingly being used in digital settings to determine who a person is based on a set of patterns. For example, characteristics like scrolling on a web page with a mouse, swiping on a web page to indicate mobile browsing, or clicks vs. hard presses.
Physiological Biometrics
- Facial measurements - Includes ear shape, eye distance, and head dimensions.
- Fingerprint - Unique ridge patterns on the fingers, widely used for authentication.
- Voice recognition – The shape and size of a person’s vocal cords as well as the pitch of their voice
- Hand geometry - Measurements of finger length, width, and spacing.
- Palm prints – Unique hand lines and palm dimensions.
- DNA - A person’s genetic sequence.
- Blood - Blood type and related markers.
- Iris and retina scans - Patterns in the eyes used for precise identification.
- Vein patterns - Unique vascular patterns in the hands or eyes.
- Heart beats and EKGs - Individual cardiac rhythms that can verify identity.
Behavioral Biometrics
- Voice - speech patterns, inflection and accents
- Typing rhythm – Unique keystroke patterns.
- Walking gait – The way a person moves or walks.
- Gestures – Specific motions made while using devices.
- Web navigation - Scrolling habits and swipe gestures.
- Signature recognition - Handwritten text or signature analysis.
- Geolocation and IP tracking – Patterns based on physical location and device use.
- Purchasing habits – Patterns of buying behavior.
- Device usage – Interaction patterns with mobile or desktop devices. For instance, how frequently a smartphone is unlocked or interacted with.
How do biometrics work? What are biometrics used for?

Let’s revisit the breakdown of the term “biometrics” into two parts: biology and metrics. Metrics involve the comparison of data sets to identify patterns and trends. Comparing a person’s biological traits against pre-stored data, or metrics, to verify their identity.
How biometrics works in technology
Here’s a simple breakdown of how biometric systems function:
- Capture - Biometric software, such as face recognition, captures the biological input provided by a user (e.g., a face scan) -- usually by prompting them to take a selfie.
- Template creation - The software measures the captured input to create a baseline data template. The biometric template is a digital representation of the distinctive characteristics extracted from a person's biometric data (such as facial features, voice, or iris patterns).
- Data storage – The biometric template is not a raw image or recording but a mathematical model that encodes the essential data points needed for comparison and verification. The template stored either on the device’s internal hardware or in a secure cloud platform.
- Matching - During subsequent use, the new biometric template is compared to the stored template. If the data matches, access is granted. Otherwise, access is denied.
Important considerations around biometrics
Templates are not images – If a hacker broke into a database of biometric templates, they wouldn’t suddenly have access to sensitive images of people nor could they recreate them based off the template.
Biometric liveness – It can detect the genuine presence of a user, rather than a physical or digital representation or an injected image (digitally manipulated images).
Key characteristics of biometric authentication
One of the most significant advantages of biometric systems is their reliance on unique, physical characteristics that cannot be easily replicated. Unlike passwords or PINs, which can be shared or stolen, biometric traits are tied directly to an individual.
This high level of security ensures that systems remain safeguarded against many traditional forms of hacking. For example, passing a face biometric check requires the physical presence of the actual person, making it incredibly difficult for unauthorized users to gain access.
However, as technology evolves, the possibility of digitally replicating biometric traits grows. This is why it’s important that systems incorporate advanced fraud prevention capabilities like deepfake and injection attack detection. Many experts also recommend combining biometrics with a second factor such as a binded device, for multi-factor authentication (MFA).
To learn more about how critical biometrics are in fighting fraud today, watch this insightful video from Frances Zelazny, CEO & Founder at Anonybit:
Types of biometric technology use cases
Today, there are a huge number of applications and services that utilize biometric technology. Here are some common examples of how people interact with physiological and behavioral biometrics in their daily lives:
- Personal hardware - Mobile phones, laptops, PCs, and tablets often enable fingerprint or facial recognition to unlock the device
- Financial transactions - Payments like wire transfers frequently require identity verification through biometrics and/or cloud-based biometrics for secure access.
- Healthcare - Biometric authentication helps healthcare providers manage patient records securely and prevent unauthorized access to sensitive information.
- Airports - Many modern airports use facial recognition to expedite passenger processing. Travelers can enroll by having a photo of their eyes and face captured, allowing faster movement through queues.
- Entertainment venues – Stadiums and other venues are beginning to offer ticketless access using face biometrics.
- Secured physical access – Biometrics are replacing key cards and PIN entries as a more secure and traceable way to authorize access to secured buildings or areas within buildings.
Biometric authentication and verification have become integral to the modern technology landscape. However, as its adoption increases across various industries, concerns around safety and privacy persist. Users often ask questions like, "What happens if my biometric data is compromised?". While passwords can be reset, biometric traits are permanent, emphasizing the need for robust data protection measures such as liveness detection. If compromised, these templates cannot be reverse engineered and are not usable by fraudsters.
For a broader overview of multimodal biometrics and their future, check out this article on multimodal biometrics.
Advantages of biometric authentication
High security and assurance
Biometrics improves security levels and assurance that a person is real by verifying their unique physiological or behavioral characteristics. It is increasingly common for users’ passwords, PINs and personally identifiable information to be compromised by a data breach, making it easier than ever for fraudsters to obtain the answers needed to pass traditional authentication methods. Introducing biometric authentication into the process adds a roadblock for fraudsters that only a real, authorized user can circumnavigate - though a fraudster may know a person uses their dog’s name and some lucky numbers for most of their online accounts, they can’t use their face to unlock an account -- especially with liveness protections to ensure the physical presence of the rightful account owner.
User experience is convenient and fast with biometrics
While the technology behind biometric authentication is complicated, from a user’s point of view it’s incredibly easy and quick. Unlocking an account in seconds with biometrics is faster than typing out a long password that has multiple special characters or receiving a PIN via email or SMA. In addition, forgetting a password is a frequent problem and point of friction for users. The chances of you forgetting your own biometrics? Never!
Non-transferable
Biometric authentication requires its input is present upon authentication. You can’t transfer or share a physical biometric digitally – the only way to utilize most biometric authentication systems is with a physical application.
Unlike passwords, PINs, and answers to security questions, biometrics are unique in that they cannot be shared – either unknowingly or knowingly (think sharing streaming passwords with a family member or a login with a co-worker). Authentication via a biometric ensures the right person.
Near spoof-proof
Biometrics like face and voice are extremely difficult to spoof. Designed to capture highly unique characteristics. advanced face recognition algorithms can achieve accuracy rates over 99.97% in ideal conditions, and the chance of two unrelated individuals having indistinguishable face templates in these systems is astronomically low. In fact, you're statistically more likely to be struck by lightning than to have someone else's face unlock your account.
Flexible and scalable
A cloud-enabled biometric system can scale dynamically as user demand grows. Versus on-device biometric systems, which is limited to the capabilities and connect-ability of a physical device, to only one user. Additionally, solutions can scale quickly and easily across applications, channels, and geographies.
For insights into how biometrics are shaping customer satisfaction and combating fraud, watch this video from Dan Slate of Wealthfront:
Disadvantages of biometric authentication
Costs
It’s no surprise that a more advanced security system would require significant investments and costs to implement. In a 2018 survey by Spiceworks, 67 percent of IT professionals cite cost as” the biggest reason for not adopting biometric authentication.” Transitioning to a biometrics authentication wouldn’t be the only thing a company would have to pay for, with 47% of the surveyed stating a need to upgrade current systems in order to support a shift to biometric authentication on their devices[2].
Data breaches
Businesses and governments that collect and store users’ personal data are under constant threat from hackers. Because biometric data is irreplaceable, organizations need to treat sensitive biometric data with increased security and caution – something that’s expensive and technically difficult to stay ahead of fraud advancements. If a password or pin is compromised, there’s always the possibility of changing it. The same can’t be said for a person’s physiological or behavioral biometrics.
Data privacy
As the world increases its use of biometric authentication systems like facial recognition technology and other biometric security measures, privacy of users needs to be taken into consideration. Ensure you work with a provider well versed in requirements and best practices such as protecting consumer data in transit and at rest using industry-standard security mechanisms and enterprise-grade encryption, creating templates to prevent reverse engineering, storing templates separately from the consumer’s personally identifiable information, and ensuring compliance with Global Data Protection Regulation (GDPR) and state regulation.
Minimizing bias
Biometric technology is not inherently biased — it is the design of biometric technology that can introduce discrimination, specifically the lack of algorithmic inclusivity, bias in feature selection, and bias in performance metrics. Look for technology that has been certified for fairness by a NIST NVLAP-accredited biometrics lab.
False positives and false negatives
A false positive in biometrics occurs when the system mistakenly grants access to an unauthorized individual. NIST tests have shown that, for face, false match rates are as low as 0.0001% in optimal conditions. However, the failure to recognize legitimate users (false negatives) may increase due to factors like poor lighting, facial obstructions, or significant changes in appearance. To address such challenges, organizations can implement secondary authentication methods, such as an additional biometric modality or another verification factor, enhancing both security and reliability.
Biometric authentication is transforming how we secure systems and data. While its advantages in security and convenience are clear, it is essential to address its limitations, particularly in privacy and cost. By staying informed and adopting emerging innovations, organizations can harness the full potential of biometric technology.
Sources
Check out more Innovator thought leadership videos
Get more insights on biometrics.
